WhatsApp Biometric Security iOS Vulnerability: Think your Face ID unlocks only your phone? Think again. This isn’t your grandma’s password protection; we’re diving deep into the surprisingly fragile world of WhatsApp’s biometric security on iOS. From sneaky bypasses to potential data breaches, we’re exposing the cracks in the system and what you need to know to keep your chats private.
This article explores the implementation of Touch ID/Face ID in WhatsApp for iOS, analyzing potential weaknesses and comparing its security to other messaging apps. We’ll dissect hypothetical attack scenarios, discuss the impact of iOS updates, and arm you with practical mitigation strategies to safeguard your private conversations. Get ready to rethink your digital security.
WhatsApp Biometric Security on iOS
WhatsApp, recognizing the increasing need for robust security measures, integrated biometric authentication – specifically Touch ID and Face ID – into its iOS app. This feature allows users to add an extra layer of protection to their chats, preventing unauthorized access even if their phone is unlocked. The implementation leverages Apple’s built-in security frameworks, offering a seamless and relatively user-friendly experience.
This integration aims to bolster the security of sensitive personal information shared within WhatsApp, ranging from private conversations and media files to financial transactions conducted through the app. The level of security provided directly correlates with the capabilities of the user’s device and the chosen biometric method.
Biometric Authentication Implementation Details
WhatsApp’s biometric security on iOS utilizes Apple’s built-in Touch ID and Face ID APIs. When enabled, the app prompts users to authenticate using their fingerprint (Touch ID) or facial recognition (Face ID) before accessing the application’s content. This authentication occurs only upon initial launch of the app or after a period of inactivity, determined by user settings. The process itself is fairly straightforward, requiring users to simply place their finger on the Touch ID sensor or present their face to the Face ID camera. The exact implementation details are not publicly available, but it’s reasonable to assume that WhatsApp uses secure enclaves and encryption to protect the biometric data.
Security Levels Offered by WhatsApp’s Biometric Features
The security offered by WhatsApp’s biometric authentication is directly tied to the security of the underlying iOS biometric system. Both Touch ID and Face ID employ sophisticated algorithms and security protocols to protect against unauthorized access. While not foolproof, these technologies significantly increase the difficulty of unauthorized access compared to a simple passcode. The security level is further enhanced by the fact that the biometric data is typically not stored on the device in a readily accessible manner, reducing the risk of data breaches. The level of security offered is comparable to other applications that use the same iOS biometric APIs.
User Experience of Enabling and Using Biometric Authentication
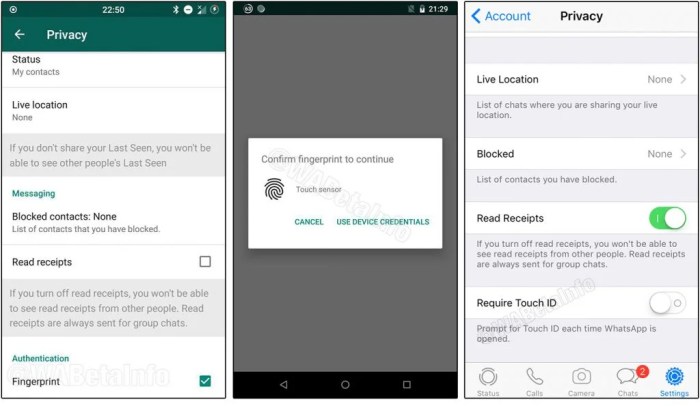
Enabling biometric authentication in WhatsApp is a relatively simple process. Users can navigate to the app’s settings, locate the “Account” section, and then find the “Privacy” settings. Within the privacy settings, an option to enable biometric authentication will be available. Once enabled, the user will be prompted to authenticate using their chosen biometric method. Subsequent launches of the app will then require biometric authentication before access is granted. The user experience is generally smooth and intuitive, mirroring the standard iOS biometric authentication flow. However, users should be aware that frequent biometric failures might necessitate re-entering their passcode, a potential inconvenience.
Vulnerability Analysis
WhatsApp’s biometric security, while intended to enhance user privacy and data protection, isn’t impervious to exploitation. The inherent complexities of software and the ever-evolving landscape of attack techniques create potential weaknesses that malicious actors could leverage. A thorough understanding of these vulnerabilities is crucial for both developers and users to mitigate risks effectively.
This section delves into potential vulnerabilities in WhatsApp’s iOS biometric security implementation, exploring scenarios that could allow for the circumvention of biometric authentication and detailing the potential consequences of successful attacks. We will focus on software vulnerabilities as the primary attack vector.
Potential Software Vulnerabilities
Software flaws are a common entry point for attackers seeking to bypass security measures. These vulnerabilities can range from minor coding errors to significant design flaws within the application’s architecture. Exploiting these weaknesses could allow an attacker to manipulate the biometric authentication process, potentially gaining unauthorized access to a user’s WhatsApp account and sensitive data. For example, a vulnerability in the code that handles biometric data could allow an attacker to inject malicious code or manipulate the authentication process itself.
Scenarios for Bypassing Biometric Authentication
Several scenarios illustrate how a successful exploitation of software vulnerabilities could lead to a bypass of WhatsApp’s biometric security. One possibility involves a sophisticated attack that leverages a zero-day vulnerability—a previously unknown security flaw—to inject malicious code that intercepts and manipulates the biometric authentication process. This malicious code might create a fake authentication response, tricking the system into granting access without requiring a legitimate biometric scan. Another scenario might involve a flaw in the application’s memory management, allowing an attacker to exploit buffer overflows or other memory-related vulnerabilities to gain control of the authentication process. This could enable them to bypass authentication entirely or to modify the system’s response to a legitimate biometric scan.
Impact of Successful Attacks
The successful exploitation of these vulnerabilities carries significant consequences. An attacker gaining unauthorized access to a WhatsApp account could intercept private messages, access sensitive files shared within chats, impersonate the user, or even compromise other linked accounts. This could lead to identity theft, financial loss, reputational damage, or even more severe consequences depending on the nature of the information stored within the account. The breach of privacy and trust is a significant concern, potentially impacting both individual users and organizations that rely on WhatsApp for communication. The scale of the potential damage is directly proportional to the sensitivity of the information shared through the application.
Examples of Potential Attack Vectors
Consider a scenario where a vulnerability in the application’s handling of biometric data allows an attacker to create a malicious application that intercepts and manipulates biometric data transmitted between the device and WhatsApp. This malicious application, perhaps disguised as a seemingly innocuous utility, could capture the biometric data, bypass the authentication mechanism, and gain unauthorized access to the user’s account. Another example involves a flaw in the application’s security protocols, enabling a man-in-the-middle attack where an attacker intercepts and manipulates the communication between the device and WhatsApp’s servers, effectively bypassing the biometric authentication process. These attacks highlight the importance of robust security measures, regular software updates, and user awareness to minimize the risk of such breaches.
Comparison with Other Messaging Apps’ Biometric Security: Whatsapp Biometric Security Ios Vulnerability
So, WhatsApp’s iOS biometric security had a bit of a stumble. But how does it stack up against other popular messaging apps? Let’s dive into a comparison to see how different platforms handle user authentication and data protection. We’ll examine the biometric methods employed, the additional security features implemented, and any publicly known vulnerabilities.
Comparing biometric security across different messaging apps isn’t just about ticking boxes; it’s about understanding the nuances of implementation and the overall security posture of each platform. Different apps prioritize different aspects of security, leading to varied approaches. This comparison aims to provide a clearer picture of the strengths and weaknesses of each app’s biometric security, helping users make informed choices about which app best aligns with their security needs.
Biometric Security Comparison Table
The following table summarizes the biometric security features of WhatsApp, Signal, and Telegram on iOS. Note that security landscapes are constantly evolving, so this information reflects the state of affairs at the time of writing. Always check for the latest updates from the respective app developers.
| App Name | Biometric Method | Security Features | Known Vulnerabilities |
|---|---|---|---|
| Face ID, Touch ID (optional, dependent on device and user settings) | End-to-end encryption for messages, optional two-factor authentication | Past vulnerabilities related to biometric bypass, particularly concerning the iOS implementation (as discussed previously). Regular security updates aim to address these. | |
| Signal | Face ID, Touch ID (optional, dependent on device and user settings) | End-to-end encryption for messages, strong focus on privacy, open-source codebase allowing for independent security audits. | Signal has a strong track record and fewer publicly known vulnerabilities compared to other apps, benefiting from its open-source nature and rigorous security practices. |
| Telegram | Face ID, Touch ID (optional, dependent on device and user settings), passcode lock | End-to-end encryption for secret chats, cloud-based storage (not end-to-end encrypted by default). | While Telegram offers robust features, the reliance on cloud storage for non-secret chats introduces potential vulnerabilities, although the app itself has not experienced widely publicized biometric-specific vulnerabilities. |
Impact of iOS Version and Updates
The interplay between iOS versions, WhatsApp’s biometric security, and the ever-evolving threat landscape is complex. Different iOS versions offer varying levels of security features and kernel protections, directly impacting the effectiveness of WhatsApp’s biometric authentication. Updates, both major and minor, can significantly alter this dynamic, sometimes patching vulnerabilities and other times, inadvertently introducing new ones. Understanding this relationship is crucial for assessing the overall security posture of WhatsApp on iOS devices.
iOS versions significantly influence the robustness of WhatsApp’s biometric security. Older iOS versions, lacking the latest security patches and improvements in kernel protection, are inherently more vulnerable to exploitation. For example, a vulnerability allowing bypass of Touch ID or Face ID in an older iOS version might be patched in a later release, rendering the exploit ineffective. Conversely, new features introduced in later iOS versions, like enhanced memory protection or improved biometric authentication mechanisms, can strengthen the security of WhatsApp’s biometric implementation. The impact is not simply binary; the difference in security between, say, iOS 14 and iOS 16, is substantial, with newer versions offering more robust defenses.
iOS Version and Vulnerability Prevalence
The prevalence of vulnerabilities impacting WhatsApp’s biometric security varies considerably across different iOS versions. Older versions, due to their lack of security updates and potential for unpatched exploits, tend to have a higher vulnerability surface area. This means that attackers are more likely to find and exploit weaknesses in older iOS versions to circumvent WhatsApp’s biometric protection. A hypothetical example might be a vulnerability discovered in iOS 13 that allowed a malicious app to bypass Face ID authentication for WhatsApp, a vulnerability that would likely be addressed in iOS 14 and subsequent releases. The regular release of security updates by Apple is a key factor in mitigating these risks, but users on older, unsupported iOS versions remain exposed.
Impact of iOS Updates on WhatsApp Biometric Security
iOS updates play a dual role in influencing WhatsApp’s biometric security. On one hand, they often patch known vulnerabilities, directly strengthening the security of the app. Apple regularly releases security updates addressing various vulnerabilities, including those that could potentially affect biometric authentication mechanisms. These updates can plug security holes exploited by malicious actors to gain unauthorized access. On the other hand, updates can sometimes inadvertently introduce new vulnerabilities, although this is less common. The introduction of new features or changes in the underlying system architecture could potentially create unforeseen weaknesses that need to be addressed in subsequent updates. The process is iterative, with constant refinement and improvement in security.
Apple’s Security Updates and Their Effect
Apple’s security updates are a critical component in mitigating vulnerabilities affecting WhatsApp’s biometric security on iOS. These updates often include patches specifically addressing flaws in the system’s biometric authentication mechanisms, making it harder for attackers to bypass these protections. However, it’s crucial to understand that the effectiveness of these updates depends on user behavior. Users must proactively install updates to benefit from the latest security improvements. Delaying or neglecting updates leaves devices and the WhatsApp biometric security vulnerable to known exploits. A timely update strategy is therefore paramount in ensuring optimal security.
Mitigation Strategies and Best Practices
So, you’re worried about WhatsApp’s biometric security on iOS? Totally understandable. While the platform is generally secure, vulnerabilities exist, and understanding how to mitigate those risks is key to protecting your chats and personal information. This section Artikels practical steps you can take to bolster your security, ensuring your private conversations remain private.
Protecting your WhatsApp data goes beyond simply relying on the app’s built-in security. A multi-layered approach, combining strong device security with mindful usage habits, is the most effective strategy. Think of it like building a fortress – you need strong walls, sturdy gates, and vigilant guards!
Strengthening Device Security Beyond WhatsApp
Device-level security is your first line of defense. A compromised device makes any app, including WhatsApp, vulnerable. This means focusing on your iPhone’s overall security posture, not just WhatsApp’s settings. A strong passcode, regular software updates, and cautious app downloads are essential components of this strategy.
Imagine a thief trying to break into your house. A weak lock (a simple passcode) makes it easy. But strong locks (a complex passcode combined with Face ID or Touch ID) make it significantly harder. Regular security updates (like iOS updates) are like reinforcing the walls and upgrading your alarm system, patching vulnerabilities before they can be exploited.
Here’s how to make your iPhone a tougher nut to crack:
- Enable a Strong Passcode: Use a long, complex alphanumeric passcode, avoiding easily guessable combinations like birthdays or sequences. The longer and more random, the better.
- Utilize Face ID or Touch ID: While not foolproof, biometric authentication adds an extra layer of protection, making unauthorized access significantly harder. But remember, these methods can be compromised under certain conditions, so a strong passcode remains crucial.
- Keep iOS Updated: Apple regularly releases updates that patch security vulnerabilities. Install these updates promptly to stay protected against the latest threats. Think of these updates as security patches for your fortress, closing holes before intruders can find them.
- Download Apps Carefully: Only download apps from the official App Store. Avoid sideloading apps from untrusted sources, as these often contain malware. Think of this as carefully inspecting visitors before letting them into your fortress.
- Enable Two-Factor Authentication (2FA) Wherever Possible: This adds an extra layer of security to your accounts, making it much harder for someone to access them even if they obtain your password. It’s like having a secondary gate to your fortress.
User Best Practices for WhatsApp Biometric Authentication, Whatsapp biometric security ios vulnerability
Beyond device-level security, your personal habits significantly impact your WhatsApp security. These best practices will help you minimize your risk.
Think of these practices as the vigilant guards patrolling your fortress. Their vigilance and attentiveness are crucial in maintaining its security.
- Regularly Review WhatsApp’s Security Settings: Familiarize yourself with WhatsApp’s biometric settings and ensure they are properly configured to your preference. This includes regularly checking and updating your biometric authentication methods.
- Be Mindful of Phishing Attempts: Be wary of suspicious links or messages that ask for your personal information. Never share your WhatsApp account details with anyone. These are the spies trying to infiltrate your fortress, and you must be vigilant.
- Use a Screen Lock: Always lock your phone when not in use to prevent unauthorized access to your WhatsApp and other apps. This is like ensuring all the gates of your fortress are securely locked.
- Consider Using a VPN: A Virtual Private Network (VPN) encrypts your internet traffic, adding an extra layer of security, especially when using public Wi-Fi. Think of this as adding an extra layer of defense to your fortress’s outer walls.
Future Implications and Research Directions
The recent vulnerability in WhatsApp’s iOS biometric security highlights the ongoing arms race between security developers and those seeking to exploit weaknesses. While patches are crucial in the short term, a proactive, research-driven approach is necessary to ensure long-term security. This involves not only strengthening existing mechanisms but also exploring innovative approaches to biometric authentication.
The discovery of this vulnerability underscores the need for a multi-faceted strategy focusing on improved authentication methods, rigorous testing, and a commitment to continuous updates. Simply patching holes as they appear is reactive; a proactive approach is vital to stay ahead of emerging threats. This requires a collaborative effort between WhatsApp, security researchers, and the broader cybersecurity community.
Enhanced Biometric Authentication Mechanisms
Several avenues exist for enhancing WhatsApp’s biometric security. Exploring alternative biometric methods beyond fingerprint and facial recognition, such as behavioral biometrics (analyzing typing patterns or scrolling behavior), could add an extra layer of security. Furthermore, implementing multi-factor authentication (MFA), requiring a combination of biometric and password verification, would significantly increase the difficulty for attackers to gain unauthorized access. This could involve integrating a time-based one-time password (TOTP) system alongside biometric authentication. For instance, imagine a scenario where unlocking WhatsApp requires both a fingerprint scan and the input of a six-digit code generated by an authenticator app. This would make brute-force attacks exponentially more challenging.
Improved Vulnerability Detection and Prevention
Proactive vulnerability detection is paramount. This involves implementing rigorous security testing procedures throughout the development lifecycle, including penetration testing and fuzzing, to identify and address potential weaknesses before they are exploited. Employing static and dynamic code analysis tools can help detect vulnerabilities early in the development process. Regular security audits by independent experts should also be a standard practice to identify any unforeseen weaknesses. The use of formal methods in software development, a rigorous approach to verifying software correctness, could also help in preventing vulnerabilities.
Continuous Security Audits and Updates
The discovery of this vulnerability underscores the importance of continuous security audits and prompt updates. WhatsApp should commit to regular security assessments, not just reacting to reported vulnerabilities but proactively searching for potential weaknesses. A rapid response system for deploying security patches is essential to minimize the window of vulnerability. This requires a streamlined update process and a robust communication strategy to inform users about critical security updates and encourage timely installation. This is crucial because even the most robust security measures are vulnerable if users don’t update their software. Think of it like a security fortress – even the strongest walls are useless if the gates are left open.
So, is your WhatsApp truly secure? The answer, unfortunately, isn’t a simple yes or no. While biometric authentication adds a layer of protection, the vulnerabilities we’ve discussed highlight the ongoing cat-and-mouse game between developers and attackers. Staying informed, updating your software regularly, and adopting strong security practices are your best defenses. Ultimately, protecting your privacy is an active process, not a passive assumption.
 Informatif Berita Informatif Terbaru
Informatif Berita Informatif Terbaru